What Is Needed for SASE?

[Editor’s note: This content was excerpted in part from Futuriom’s Secure Edge and SASE report and the 2020 SD-WAN Growth report and 2021 SD-WAN Growth report]
Secure access service edge (SASE, pronounced “sassy”) or simply Secure Edge is quickly gaining momentum in cybersecurity and networking technology circles as the shiny new object in tech. So what's new and different about it?
Actually, SASE isn’t a single technology, but the integration of several existing cybersecurity technologies that are starting to merge with software-defined wide-area networking (SD-WAN) market. Some tech marketeers are downplaying SD-WAN now, but that's not really fair. It was the innovation of SD-WAN as a cloud-based service delivery platform that made SASE possible. SD-WAN platforms can now deliver SASE functionality.
What's in SASE
The original SASE term, attributed by many to the Gartner Group consultancy, describes the blending of security technologies such as zero-trust network access (ZTNA), cloud access security brokers (CASBs), cloud-based firewall-as-a-service (FWaaS), and Secure Web Gateways (SWGs) combined by networking management provided by SD-WAN.
This all means that networking and security are converging at the network edge — the place in a cloud infrastructure closest to the end user or endpoint device — leading to a new breed of edge security technology.
The need for this convergence is well understood. Widespread adoption of mobile devices and cloud-based services, along with the ongoing COVID-19 pandemic, have pushed the workplace into remote locations and opened the way for a universe of unmanned devices — the Internet of Things (IoT). In this increasingly dynamic and rapidly growing environment, old methods of IT connectivity and security have at times fallen short of orchestrating and protecting digital resources.
Why SD-WAN Is Key to SASE
SD-WAN has played a major role in digital transformation and the move to cloud infrastructure because it offers a software-defined architecture for deploying and managing networking and security resources and functions. The design of SD-WAN, in other words, makes the SD-WAN service edge an ideal control point for security functions — the foundation point of SASE/Secure Edge.
According to Futuriom’s June 2020 SD-WAN Growth Report, and as shown in the chart below, security is among the top benefits of SD-WAN, in addition to better management/agility, bandwidth optimization/cost savings, and faster cloud performance.
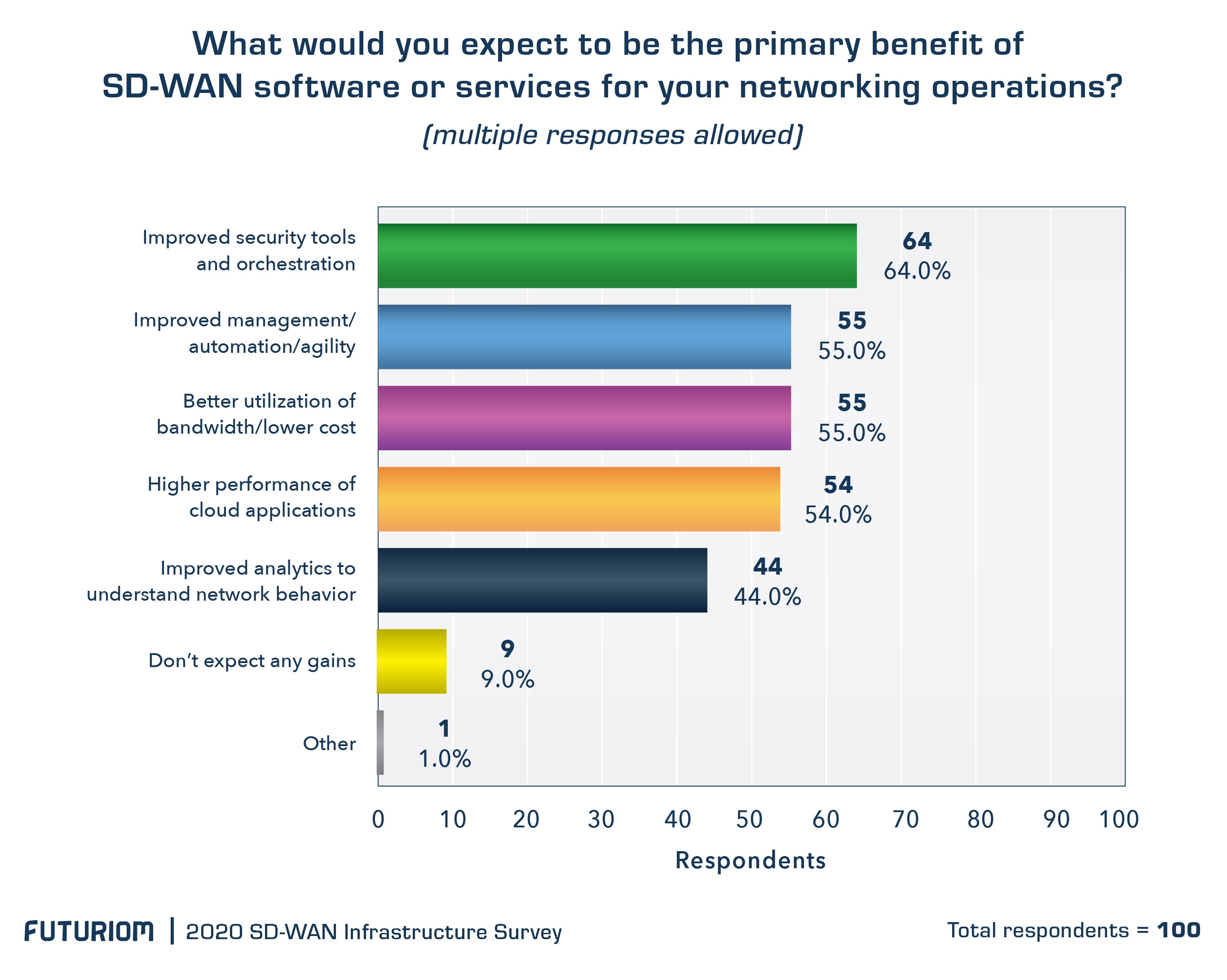
The result of SD-WAN’s popularity is a market now in the billions of dollars. SD-WAN is a technology that has delivered on its promise. But this doesn’t mean SD-WAN solves every problem. Cybersecurity is still a dynamic problem that has its own area of expertise – with many niches and discrete functions -- for the foreseeable future. But security does need to be better integrated into the network fabric, and that is where SASE and the Secure Edge come in.
Defining SASE/Secure Edge
As we have noted, a key element of SASE/Secure Edge is that the security capabilities are delivered primarily as cloud-based services over SD-WAN. This is why industry consortium MEF, which has attempted to create standards around SD-WAN, defines a SASE service as "a service connecting users (machine or human) with their applications in the cloud while providing connectivity performance and security assurance determined by policies set by the Subscriber."
Meeting these needs requires a converged networking and security framework that can be used by both service providers and enterprises. This framework defines SASE/Secure Edge services, which would be used to connect and secure digital assets regardless of their location.
Issues that SASE must Solve
Implementing SASE and Secure Edge calls for rethinking how network and security are addressed, especially since enterprises have spent years positioning the data center as the hub of network security and have configured network traffic flows accordingly.
But the pressure is on most enterprises to make the shift. Today’s typical user is outside the corporate data center and needs resources that exist in a cloud environment. This means the private data center is no longer the physical and logical core of the enterprise network — nor of its security infrastructure.
Distributed networks have complicated security issues. Considerations include the proper placement of security platforms, devices, and agents; the best way to reduce risk with remote users, or worse yet, with contractors who might not even have a laptop agent; and how best to provide enterprise-wide policy regarding authentication, authorization, access control, and security based on identity and current security posture in the cloud.
SASE/Secure edge delivered via SD-WAN addresses these issues by decreasing the need for backhaul of data to a central location; optimizing routing of data traffic; and allowing for cloud-delivered security resources over the same platforms that deliver traffic via SD-WAN’s endpoint-focused implementation.
Rather than forcing traffic back to the datacenter for inspection, Secure Edge and SASE services can place inspection engines at nearby point of presence (PoPs). Endpoints connect to local PoPs based on identity and context, and traffic is inspected and forwarded as appropriate through the Internet or provider backbone. The design connects fixed and mobile users, whether managed or unmanaged, with resources in traditional private data centers or in the cloud.
As more mission-critical applications migrate to the cloud, the need to address security and quality-of-service issues, such as latency, will only increase. This need for highly secure, low latency, access to digital assets regardless of location requires a tight integration of networking and security capabilities. Secure Edge and SASE can deliver on this promise by integrating cloud-based security services with a global fabric of points of presence that leverage SD-WAN.
SASE Suppliers
SD-WAN is ground zero for SASE and Secure Edge development, as larger companies as well as startups buy, merge, or continue to build out their portfolio to position themselves for the convergence of SD-WAN and SASE.
Large network equipment vendors that have built or bought their way into the market via SD-WAN include Cisco (Viptela), Nokia (Nuage Networks), and HPE (Silver Peak). Virtualization giants with SD-WAN offerings include VMware (VeloCloud) and Citrix, which also happen to be building secure virtualized environments – VMware with Workspace Security and Citrix with Workspace and Citrix Cloud.
Large security vendors have also entered the space. It is notable that two leaders in the firewall market -- Fortinet and Palo Alto Networks -- have made key moves to expand their SD-WAN offerings, with Fortinet building an SD-WAN product internally and Palo Alto buying Cloudgenix. A range of security companies offering CASB, SWG, FWaaS, and ZTNA in the cloud are all stepping up to the SASE plate.
Emerging venture-funded vendors with SD-WAN and security offerings have also evolved to expand their security focus. These include network as-a-service (NaaS) vendors Aryaka Networks, which offers a full security portfolio on its network including virtual firewall support from both Palo Alto Networks and Check Point, as well as management of both physical and virtual firewalls.
Another security-focused NaaS supplier is Cato Networks, which takes the thin client approach to SD-WAN coupled with a powerful suite of cloud security offerings. Secure Edge, SAAS, and SD-WAN vendor Versa Networks offers a multi-tenant SD-WAN platform with its own suite of security services. Versa also offers a cloud-managed remote security service called Versa Secure Access, part of its Versa SASE offering.
Finally, there are numerous pure play SD-WAN vendors in the market that will need to make Secure Edge plays. Others SD-WAN players to watch include Bigleaf Networks and FatPipe Networks. Going forward, as the SD-WAN market consolidates, the capability to deliver full- fledged SASE/Secure Edge functionality with SD-WAN capabilities is going to be a key differentiator.